@read@blog.nigini.me I still microblog.pub even though I have two problems:
- memory is getting low on my host running all the services I'm using (4GB RAM)
- time needed to maintain microblog.pub beside #GoToSocial.
But it's still worth it I guess - otherwise I wouldn't have made the #yunohost package version 2 to keep #microblogpub available for yunohosts next version.
BTW: for yunohost a database integration would be great - there's always running mariadb.
I looked at this again and found that the two notes requested very often from my #microblogpub are those that I 'pinned' that can be found at /featured.
The rest are paths pointing to information about this side. Maybe it has been some kind of #fedibot?
Here's a #fail2ban config that helped me blocking the IPs:
# cat /etc/fail2ban/filter.d/manual.conf [Definition]
# cat /etc/fail2ban/jail.d/manual.conf [manual] enabled = true bantime = 14d
This seems to lead to a jail which isn't connected to a logfile and for which manually added IPs stay blocked for 14 days.
To block IPs I used fail2ban-client -vvv set manual banip $IP which leads to
# fail2ban-client status manual basic Status for the jail: manual |- Filter | |- Currently failed: 0 | |- Total failed: 0 | `- File list: `- Actions |- Currently banned: 4 |- Total banned: 4 `- Banned IP list: 34.229.130.24 44.206.236.255 54.164.161.50 3.238.157.198
fail2ban is integrated into my #yunohost and even though it doesn't come with the greatest documentation I'm starting to love it.
If you can read this you're not affected by the following …
This #microblogpub had some load recently and I looked into it. I looked through the logs and counted the connections from each IP. These are the IPs with the highest volume:
89 192.168.2.20 385 202.61.242.89 417 65.21.187.247 433 141.95.205.35 275698 34.229.130.24 287955 44.206.236.255 297312 54.164.161.50 304990 3.238.157.198
The last for look suspicious. I looked at the kind of request that added up to those comparative high numbers:
13 /.well-known/host-meta 13 /.well-known/webfinger?resource=acct:chrichri@chrichri.ween.de 22453 /o/350ab61e097f4c89bbe53836f0f5d1f6 24681 /followers 24684 /following 24684 /outbox 313796 /o/72327fd24abe48bb82564144dcee1ba6 313803 /featured 336225 /.well-known/webfinger?resource=acct:me@chrichri.ween.de 336243 /
All quite common, but one of the highest counts gets one note. All of these accesses from four IPs only within less than a day.
The article that seems to be so interesting is about @midzer@chaos.socials work for flohmarkt and the fact that he can be sponsored via #github.
The four IPs are all at Amazon:
24.130.229.34.in-addr.arpa domain name pointer ec2-34-229-130-24.compute-1.amazonaws.com. 255.236.206.44.in-addr.arpa domain name pointer ec2-44-206-236-255.compute-1.amazonaws.com. 50.161.164.54.in-addr.arpa domain name pointer ec2-54-164-161-50.compute-1.amazonaws.com. 198.157.238.3.in-addr.arpa domain name pointer ec2-3-238-157-198.compute-1.amazonaws.com.
I blocked the four IPs to get the load back down to a value below 1.
If you can't read this or you'd have a clue why those IPs constantly access those few URLs - please let me know!
If you can read this you're reading a note created on my #microblogpub instance on my #yunohost.
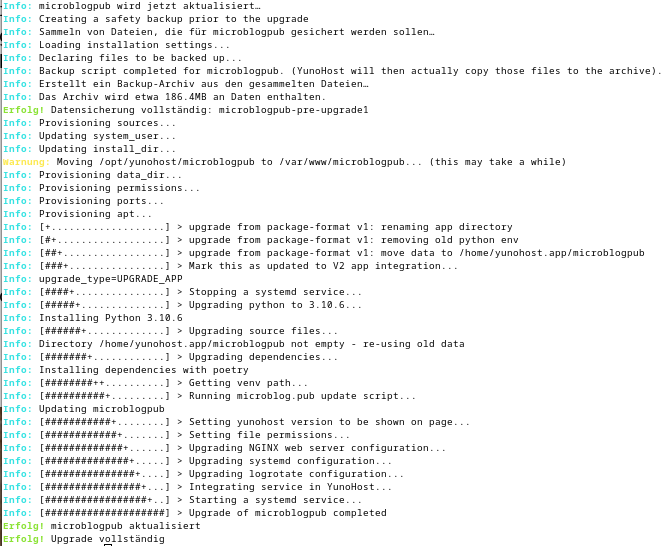
@t@hexa.ninja the author of microblog.pub created an integration for yunohost in package format version 1.
yunohost moved on and created the packaging format version 2.
Building on the work of Thomas I upgraded the package to the newer packaging format and integrated it into yunohosts app catalogue where it will appear within the next 24h.
If you're using microblog.pub on a yunohost you'll be offered an update of the app once it has been included into the catalog.
Thanks Thomas for that great software!
(This note is my first one written on my updated microblog.pub v2 integration on yunohost.)
Finally looked into the options to change the appearance of my #microblogpub microblog.pub this note is written on.
Nice . Using #firefox to tinker with the colours on the opened page and change the css I drafted some changes.
I put the color changes into data/_theme.scss, but overriding the layout of dd/dd to not contain nowrap in dl { didn't work that way. I had to change that in app/scss/main.scss which I believe is not meant to be done this way.
I guess there must be some way to override the settings from app/scss/main.scss somewhere in data/ to seperate code and configuration.
Maybe someone or even @dev@microblog.pub could shed some light onto this.
I started this instance in September 2022 and I've gotten very used to it and wouldn't want to miss this great application and its near perfect balance between simplicity/being light and offering exactly the feature set I like to have.
Did you already stumble over #microblogpub? Best solution for minimalists I found.
The #yunohost running this #microblogpub instance runs on a #RockPro64 in a #Pine64 nas case.
I started a year ago by installing it on an eMMC as a yunohost test, added two sata SSDs and now decided to simplify the setup by removing the eMMC boot medium.
Booting of the #SoftwareRaid configured on the SATA SSDs turned out to be less easy then I'd expected and I ended up preparing a #howto about doing this remote via ssh.
https://git.sr.ht/~chrichri/RockPro64_u-boot_SATA_software_RAID_howto
Letztes Jahr habe ich es nicht geschafft, aber dieses Jahr ist es fertig geworden: Unser #Gründach.
Inzwischen ist schon etwas Sedum über die Angelegenheit gewachsen.
#ShotOnLibrem5, bearbeitet mit #ImagePipe veröffentlicht in #microblogpub in #tangram
@t@hexa.ninja , thanks for the hide shares button and for the ongoing work for further filter functions!
#microblogpub becomes better and better!
One of the best aspects of being #selfhosted on #microblogpub is that I do not have to follow the discussions about blocking who and why.
I'm free to read whatever I care if I get across it.
No disturbing timeline that shows me stuff I didn't ask for.
I already liked that at social.librem.one by #purism.
This is another step towards independency and using #yunohost this is until know hosted on my home internet access without problems.
I didn't care, yet, to carry the #rockpro64 nas case to a sever housing. I even didn't care, yet, to extend disk space on the 16gb emmc to the ssd I put into its case...